Cyber Threat Intelligence Intro

Cyber Threat Intelligence is evidence-based knowledge aimed at informing you about adversaries, including their indicators, tactics, motivations, and actionable advice against them. This data helps security professionals to tune their defenses and allows for better decision making.
Threat Intelligence can also be classified into 3 types of Intel:
- Tactical - covers Tactic, Techniques, and Procedures used by a threat actor
- Operational - actionable intel that falls in line with a companies needs
- Strategical - high-level intel which impacts the business aspect of an organization
Based on the adversary, we can determine their TTPs, Behavior, and indicators through the MITRE AT&CK framework. We can also find an APT(Adversarial Persistent Threat) through this database as well.
We can also follow The Cyber Kill Chain which is a framework for determining what step an adversary is in achieving their objective.

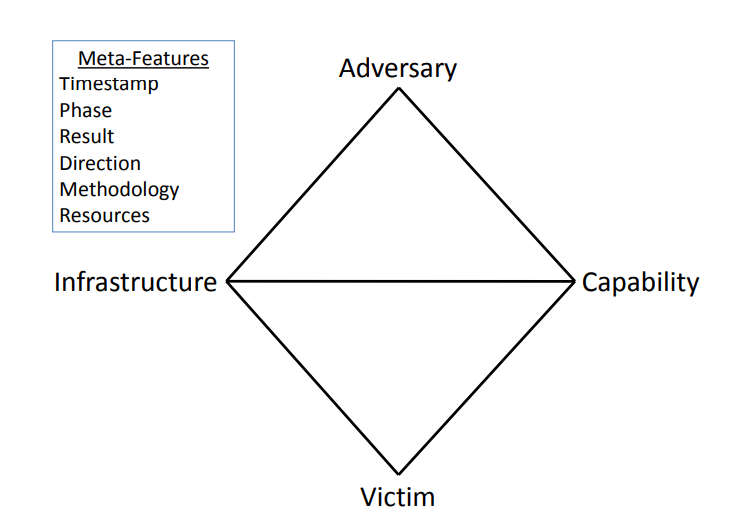
The Diamond Model also allows us to pivot along its properties to produce a complete picture of an attack and correlate indicators.
Collection of CTI Resources and Platforms:
Abuse.ch - for tracking malware and botnet indicators
Talos Intelligence - provides actionable intelligence, visibility on indicators, and protection against emerging threats through data collected from Cisco
VirusTotal - for detecting known malware from IPs, Domains, and URLs
The Hive - an open-source Security Incident Response Platform
- Collaborate | Elaborate | Act - 3 Core functions of The Hive
- Key features include Case management / Alert Triage / Cortex (analysis) / Active Response / Custom Dashboards / Built-in MISP int.
- you can also integrate DigitalShadows2TH & ZeroFox2TH (open-source alert feeders)
OpenCTI - an open-source platform designed to provide organizations with the means to manage CTI through the storage, analysis, visualization and presentation of threat campaigns, malware and IOCs. - OpenCTI Install
MISP (Malware Information Sharing Platform) is an open-source solution for collecting, storing, distributing and sharing cyber security indicators and threats about cyber security incidents and malware analysis - MISP Install
- CIRCL (Computer Incident Response Center Luxembourg) also provides free training materials
These tools work in tandem with the MITRE ATT&CK framework which was created to document and track techniques that adversaries use. You can also look at an adversaries behaviors and targets.
You can also reference threat reports from Mandiant, Recorded Future and AT&TCybersecurity.